Introduction
Cosmic objects emit different kind of electromagnetic waves. Radio waves, which are used for communication in wireless networks, are a kind of electromagnetic waves. The frequency bands for wireless networks are between 2.5-5 GHz. Wireless networks are becoming more popular by each passing day due to their inherent [“wire-less-ness”] ease of installation and connection. White (2016) designates wireless as one of the most popular protocol for implementing local area networks (p. 194). In this paper, we will discuss different topology options that network architects have when designing a wireless network.
Wireless Topologies
Important components of a wireless network usually include [but not limited to]; network interface card (NIC) and a wireless access point (WAP). A traditional NIC does not support connecting to a wireless network. Therefore, a special kind of NIC is needed which Weaver, Weaver and Farwood (2014) called Wireless NIC (WNIC) (p. 232). A WAP on the other hand can be either a “Wi-Fi” capable router or a special kind of device that is meant to add wireless capability to an existing wire-based network. IEEE introduced 802.11 standard is the most commonly used protocol for wireless networks.
Three kinds of wireless network topologies are (i) Point-to-Point, (ii) Multipoint-to-Point, and (iii)
Point-to-Point (p2p) Topology
p2p is the most preferred way of communication when two wireless devices need to exchange data. The most common application of a p2p connection is how remote controls communicate with the controlled devices. The communication takes place using infrared (IR) waves.
Another scenario where p2p communication can be used is internet-of-things (IoT), where very often two devices need to communicate with each other directly without any third-party involved. Bluetooth, which is a radio waves based wireless communication, can be used to establish p2p connection.
p2p networks are usually slow and only one device can send data at a time (half duplex mode). Another disadvantage of using a p2p topology is security, where a source device can push malicious things into the target device without the target device knowing
Multipoint-to-Point (mp-2-p) Topology
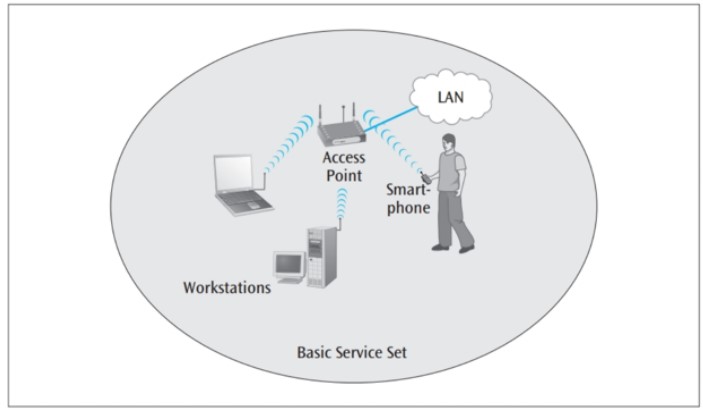
This is the most common topology for wireless local area network (WLAN). In this topology, several user devices compete with each other to communication with a WAP over a shared frequency band (See Figure 1). The topology used frequency division multiplexing (FDM). Sivabalan (2019) defined FDM as a way to effectively manage bandwidth through non-overlapping frequency bands.
The wireless LAN standard name for this kind of setup is Basic Service Set (BSS).
This is the most preferred topology when setting up a wireless network in an area of less than 2500 square feet, such as in a house or small building.
Securing this kind of networks is a challenge. Although several schemes for encryption and security exist but almost all of them are “hack-able".
Point-to-Multipoint (p2mp) Topology
In many cases, an organization likes their wireless network to cover a significant area. Therefore, in order to maintain coverage multiple WAPs are strategically placed, where each WAP serves a certain area (See figure 2). This kind of setup is referred to as Extended Service Set (ESS).
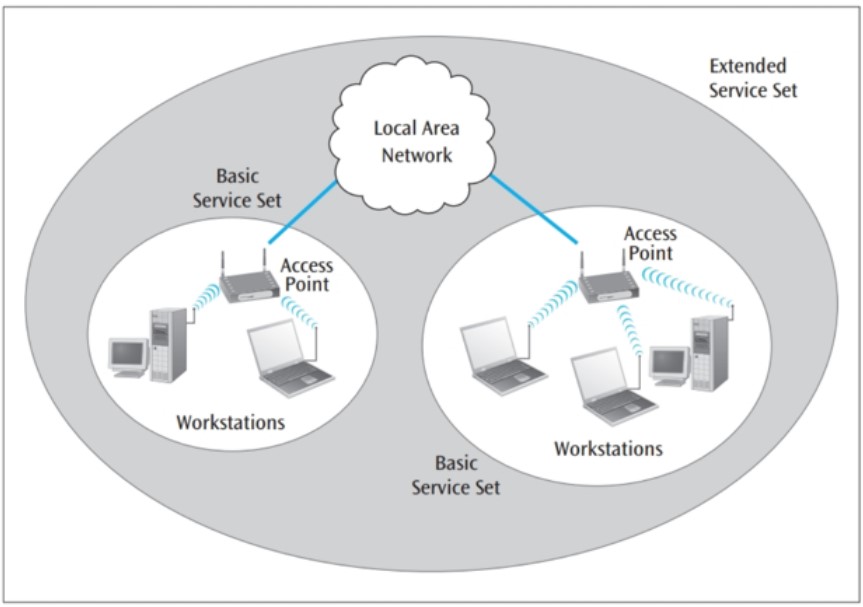
All cellular networks use this topology, as they want their consumers to access their services without interruption when they are moving
This kind of networks is expensive to setup and maintain. Security is also a concern, especially for the networks that use the IEEE 802.11 standard (ElectronicNotes, 2019).
Conclusion
We discussed different kind of topologies, figuring out the best depends on multiple factors that include environment, scale, budget and strategic goals of the organizations. The most suitable topology for small networks is the multipoint-to-point. However, in order to implement it efficiently, security and coverage should be effectively planned.
References
White, C. (2016). Data communications & computer networks (8th ed.). Boston, MA: Cengage Learning.
Weaver, R., Weaver, D., & Farwood, D. (2014). Guide to network defense and countermeasures (3rd ed.). Boston, MA: Cengage Learning.
Sivabalan, V. (2019). Frequency-division multiplexing: advantages & examples. Retrieved from https://study.com/academy/lesson/frequency-division-multiplexing-advantages-examples.html
ElectronicNotes (2019). Wi-Fi security: WEP & WPA/WPA2. Retrieved from https://www.electronics-notes.com/articles/connectivity/wifi-ieee-802-11/security-wep-wpa-wpa2.php

