The transmission on wireless networks is primarily done using electromagnetic (EM) waves. Lets quickly develop an understanding of EM waves.
ELECTROMAGNETIC COMMUNICATION
Cosmic objects emit different kind of energy, that energy is called electromagnetic radiation. The radiation is made up of electrical and magnetic fields and it travels as waves. These waves can be used to transmit information using distinct and repeating patterns of disturbance.
Electro magnetic waves can be of several types. In wireless communication, we are only concerned with Infrared and Radio waves.
Infrared vs Radio Communication
Infrared rays are used for transmission in some cases, for example in remote control sensing. However, the most popular transmission method is radio frequency (RF) transmission. The common frequency bands used for wireless communication are between 2.5 – 5 GHz.
802.11 Standard
IEEE introduced 802.11 standard that is most commonly used protocol for wireless communication.
COMPONENTS IN WIRELESS COMMUNICATION
The wireless communication is heavily dependent on Media Access Control (MAC), which is a sub-layer of Data Link Layer. Some components of a wireless network include access points, wireless network interface cards (NIC) and antennas.
Access Points (AP)
AP serves two purposes, first it let stations connect to the wireless network and second it extends a wired network to add wireless capabilities.
Wireless NIC
Using a wireless NIC, a station connects to a wireless network.
Antennas
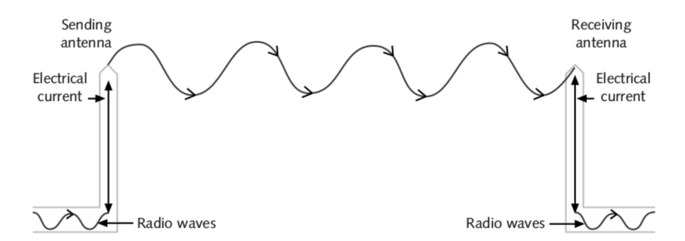
Antennas are used to transmit and receive RF waves. They use electrical current to produce an oscillation that matches the frequency of the received or to be transmitted RF wave.
Threats to Wireless Networks
A hacker can launch active or passive attacks on a wireless network since the communication is happening through RF waves that are present in the environment.
Passive Attack
In a passive attack, the hacker listen a wireless channel without being detected.
Active Attack
In an active attack, the hacker sends a probe frame to the AP and gathers information about the network. Its easy to detect an active attack. Some kinds of active attacks are similar to DoS & DDoS in nature, such as jamming, association flood and forged dissociation. Brute force and dictionary type active attacks can be launched on a wireless network.
Measures to Secure a Wireless Network
A good wireless network security policy can cope with these threats. The security policy should entail physical as well as virtual measures. Several measures can be taken to secure communication between AP and connected stations.
Authentication & Authorization
In order to join a wireless network, a station first have to authenticate itself. WEP, WPA and WPA2 are some authentication methods available for wireless networks.
WEP is an obsolete method, which operates on pre-shared key principle; WPA operates on temporal key principle where each packet has its own encryption key. WPA2 uses AES and temporal keys.
In addition to authentication, authorization can be used to add another layer of access control before a station can become part of a wireless network. Kerberos and RADIUS are some methods of authorization.
Strategically Placing APs
Consider placing APs strategically to ensure that the coverage area does not exceed that physical perimeter of the organization.
Physical Security
Last but not least, physical security should be ensured. For instance, the wireless devices that are allowed to join a wireless network should always remain in the premises. This way hackers won't be able to install any malicious stuff on the device, thus chances of compromise are lesser.
Conclusion
RF waves are used for communication in a wireless network. The wireless networks make it easier to connect to internet. But since it is easy to intercept the RF waves, the wireless networks are more vulnerable than wired networks. Therefore proper measures should be in place to avoid any security and privacy compromises.

