There are several kind of attacks that can be used to compromise a web application and steal the sensitive data from it. In this article, I will go over some of them and how to foil them. Note that the example web application scripts are written using Python 3.
Shell Shock Attack
A web application is responsible for entertaining different kinds of incoming HTTP requests. A HTTP request has two components header and payload. A complex web application can be configured to deal with custom headers. Each custom header may convey a specific instruction for the web application.
In a shell shock attack, the hacker sends a malformed value for a custom header which results in execution of malicious code in the context of the web application.
HTTP/1.x 200 OK
....
Content-Type: text/html; charset=UTF-8
Last-Modified: Sat, 28 Nov 2009 03:50:37 GMT
Custom-Malicious-Header:
Defense
The defense against this kind of attack is to sanitize custom header values and ensure that the web application is not naive enough to execute the malicious code defined in the header.
Cross Site Scripting (XSS) Attack
A XSS attack is one of the most common attacks that hackers stage against a web application. In a XSS attack, the hacker sends a malicious payload in the HTTP request to the web application. The target web application executes the malicious payload inside its own context, that cross site aspect of a XSS attack.
Consider following HTTP GET request
GET http:/target-host/?name=<script> alert(document.cookie);</script> HTTP/1.1
And lets say the web application renders the payload on the HTML page
import urllib.parse as urlparse
parsed = urlparse.urlparse(url)
name = urlparse.parse_qs(parsed.query)['name']
print '''<html>
<head><title>My first Python CGI app</title></head>
<body>
<p> {} </p>
</body>
</html>'''
.format(name)
In above scenario, the hacker was able to execute a malicious script through XSS attack.
Defense
The primary defense against XSS is sanitizing. Sanitizing entails escaping sequencing and validating the input against a pattern. The above application code can be rewritten as
import urllib.parse as urlparse, cgi, re
parsed = urlparse.urlparse(url)
name = urlparse.parse_qs(parsed.query)['name']
# escape the special characters
escaped_name = cgi.escape(name)
''' match using regex if the name only contains alphabets,
numbers and spaces '''
pattern = re.compile("^([A-Z ][0-9]+)+$")
if pattern.match(escaped_name):
print
'''<html>
<head>
<title>My first Python CGI app</title>
</head>
<body>
<p> {} </p>
</body>
</html>'''
.format(escaped_name)
else:
print 'Name not valid'
See how we escaped special character such as < and>. We also used a regular expression to ensure that the name only contains number, alphabets and spaces.
Another way to foil XSS is to define a content security policy that establishes what sort of content can be rendered through user input. Many web applications use a predefined content grammar language such as Markdown.
Session/Cookie Hijacking
A very common type of attack is session hijacking attack. In this kind of attack, an attacker gets access to an authenticated session key which has been issued to a client by the web application after completing all authentication and authorization procedures. Anybody with that session key can make requests to web application resources. The session key can be stolen through number of method including XSS or man-in-middle attack. The picture below shows a scenario where the attacker has stolen the session key using man-in-middle attack, then he is using that stolen key to access web application resources.
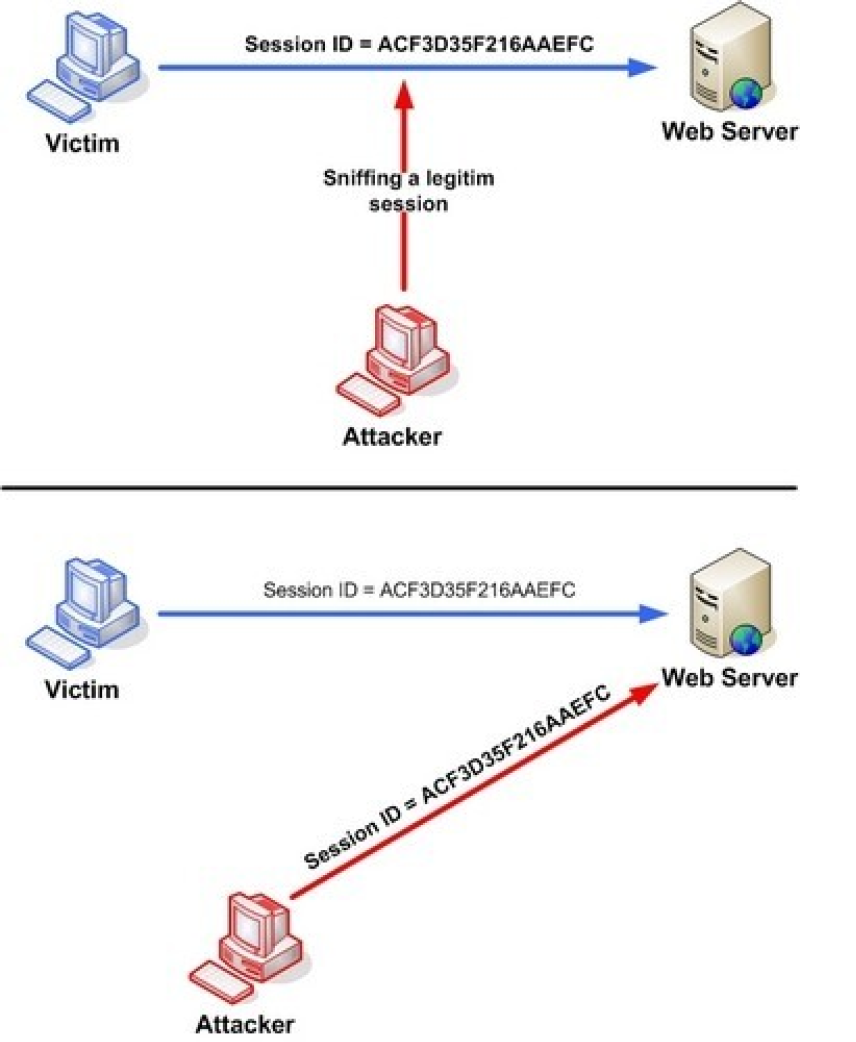
Defense
There are a number of defenses against this kind of attack.
- 1. The session key is stored in a web browser cookie. If
the cookie is enabled for multiple domains, it is
vulnerable to XSS attacks . Using LocalStorage fixes this
problem.
- 2. Using encryption such as Transport Layer Security (TLS) to encrypt the communication between the server and the client. This way man-in-middle attack can be foiled.
- 3. Authenticating every request through use of a signature. The signature is generated using following mathematical equation;
signature = f(secret key, message)
If the signature doesn't match the request is not honored. Amazon S3 uses this kind of authentication.
GIFAR or PDFAR Attack
JAR files can be embedded into a GIF or PDF file and executed using HTML

