Introduction
A computer network is an integral feature of any IT infrastructure and plays a vital role in establishing communication channels between different components of the infrastructure (White, 2016). A computer network can be as simple as two workstations connected with each other via a cross cable or as complex as billions of geographically dispersed nodes and workstations such as Internet. Managing a computer network is one of the primary responsibilities of a network administrator and it becomes a challenge often. Network management at its simplest is the exchange of messages between a controller and nodes and workstations to ensure the latter two are working as expected. In this paper, we will discuss tools and techniques for managing a computer network especially in terms of policy compliance, bandwidth management and assets management.
Policy Compliance
In cyber security, policy establishment falls under the realm of administrative controls. The other two controls (i.e. physical security and technology controls) have to comply with whatever has been defined in the policy.
At the technology controls, level policies can be enforced using firewalls and IPS (Intrusion Prevention Systems). At the IPS level, Cisco coined the idea of next-gen IPS (NGIPS) and introduced a new product called Firepower. A traditional IPS only provides insights into the threats, whereas an NGIPS provides visibility into the network context (and infrastructure), which often involves remote components as well. In synopsis thecore features of Firepower include insights into virtual or cloud applications, endpoint communication, client-side applications, virtual machine communication, malware detection, automation using AI and impact assessment. From a policy compliance perspective, this network context knowledge helps in defining and ensuring granular and high-level security policies (Cisco, 2018).

A NGIPS along with a Firewall is the best option for policy compliance however the policy compliance can be ensured through basic means of establishing policy based rules in a router that connects the organization to external world.
Using AI in Policy Compliance
In recent years, AI has been used to aid in policy compliance. Although AI in cyber space is still in infancy stage but it has already produced good results in detecting malware connection to an unknown, connection to a malicious domain, port scanning & stolen data exfiltration (Chuvakin, 2018).
Bandwidth Management
Bandwidth management is broken down into two parts (i) bandwidth monitoring, in which all the devices (nodes and workstations) on a network are monitored for bandwidth utilization (ii) setting bandwidth cap and throttling, where bandwidth utilization limits are enforced. Bandwidth management helps in limiting traffic congestion situations as well as keeps the network costs in budget. Bandwidth management policies are defined in the administrative controls.
A bandwidth management framework can be as simple as measuring bandwidth using SNMP (Simple Network Management Protocol) and establishing caps in routers and switches or as complex as using cloud management tools. If an organization opts for using the latter, Cisco Meraki is a robust framework that helps in establishing bandwidth caps using a cloud based management system (Meraki, 2018). Figure 2 depicts the Meraki cloud’s bandwidth management console.
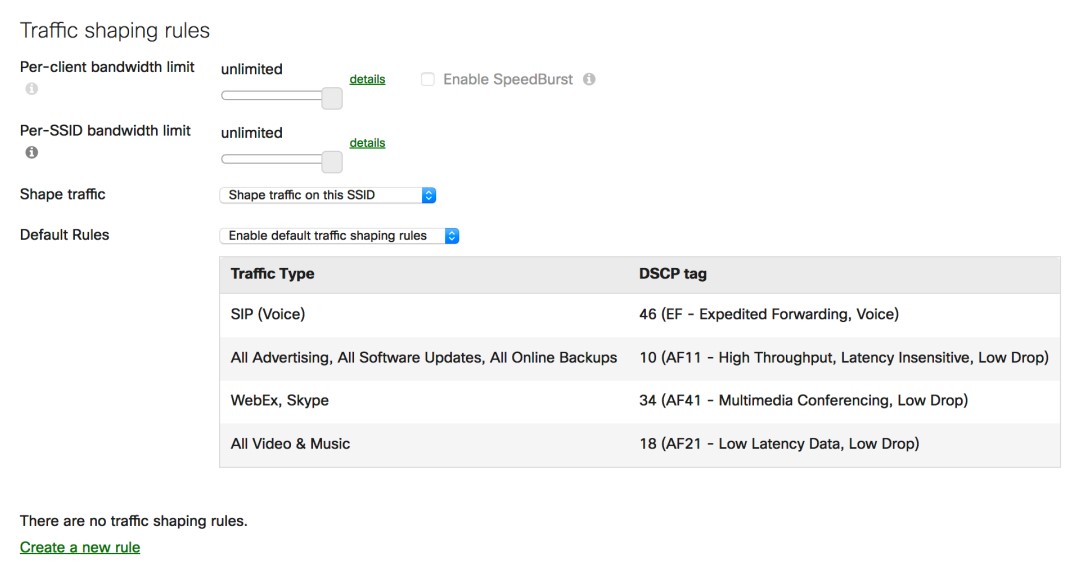
The question of what is the best tool for bandwidth management can only be answered in context of organization’s size and budget commitment. For a small organization using routers and/or switches for establishing bandwidth management is suitable whereas a large organization can consider using cloud based infrastructures like Meeraki which essentially offers much more than just bandwidth management.
Assets Management
Assets management is one of the critical tasks in network management. The asset management includes activities such as maintaining a inventory of network devices (nodes and workstations) and ensuring that they are managed through a life cycle.
One of the most popular tools for asset management is Netscout’s nGeniusOne. It helps in maintaining an inventory of the network assets and their status by integrating with protocols such as SNMP. It is a cloud based service and was listed by Gartner as 2018’s leading platform for network infrastructure management. Asset management can be implemented by using open source tools that communicate with devices using SNMP protocol.
Organizations can opt for an expensive tool such as nGeniusOne or do things in a cheaper way using free open source tools, the choice again is a contextual thing.
Can one tool be used in multiple management areas?
Most of the cloud management tools offer an end-to-end network infrastructure management framework therefore; they can be used in multiple management areas. For example, Meraki can be used for bandwidth management, asset management and policy compliance. Non-cloud components can be used in multiple areas as well. A router, for instance, can be used in policy compliance and bandwidth management.
Part of the reason is the fact that policy compliance, bandwidth management and assets management are closely related to each other.
Conclusion
We covered different areas of network management and explored some tools and techniques used in each area. Answer to the question of best tool in each area is contextual, for example, a large organization can opt for a tool that is easily scalable and centralized but expensive, on the other hand a small business can do network management using different means that fit in their budget. We also touch based on how AI is being used in policy compliance, though it is in infancy stages.
References
White, C. (2016). Data communications & computer networks (8th ed.). Boston, MA: Cengage Learning.
Cisco (2018). Next-Generation Intrusion Prevention System (NGIPS). Retrieved from https://www.cisco.com/c/en/us/products/security/ngips/index.html
Chuvakin (2018). Traffic and Bandwidth Shaping. Retrieved from https://documentation.meraki.com/MR/Firewall_and_Traffic_Shaping/Traffic_and_
Meraki (2018). Network Anomaly Detection Track Record in Real Life? Retrieved from https://blogs.gartner.com/anton-chuvakin/2018/10/15/network-anomaly-detection-track-record-in-real-life/

