A buffer overflow attack simply putting is a vulnerability that potentially exists in C and C++ programs where a variable can exceed it's bounds and write into the contagious memory location. C and C++ doesn't perform bound checking on variables defined in a program. In order to understand buffer overflow, we first need to understand memory stacks.
Memory Stack
A stack is a special region in your memory that holds variables created by each function. Stack is a LIFO data structure and the CPU closely supervises and manages it. Every time a function declares variable, it is pushed on the stack. When a function exits, all variables pushed to the stack by that functions are cleared. The CPU manages the stack for you, therefore stack is a managed memory architecture.
EBP and ESP
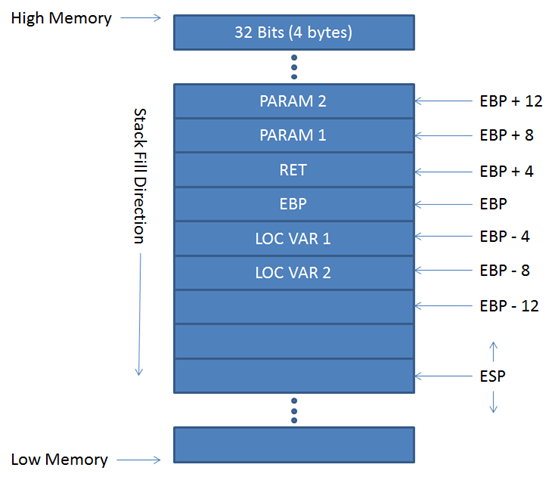
A stack data structure has two important components, EBP and ESP. When you call a function (such as main), a space is allocated on the stack for all local variables in that function. That space is referenced using EBP.
ESP on the other hand is the used to current position on the stack you are.
EBP can be thought of a point of reference. For example that if a local variable for a program is stored at a particular location in the stack, it is referenced using EBP + N, where N is the distance of that location from EBP.
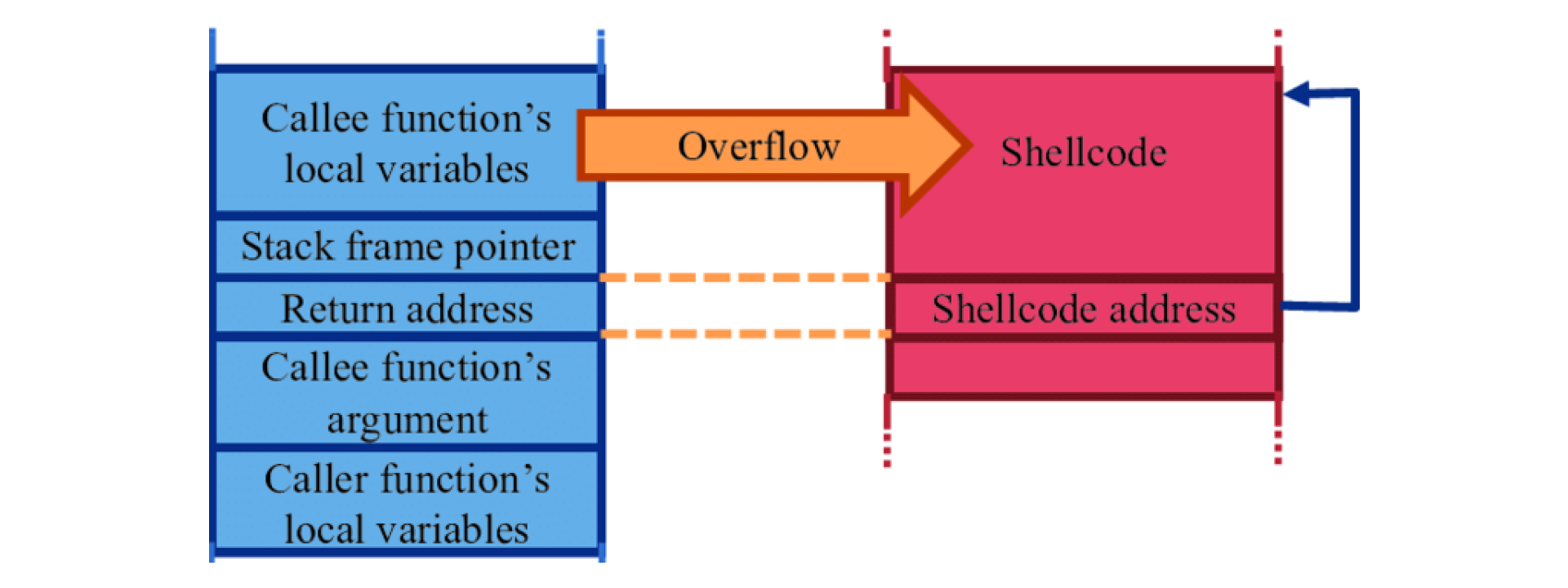
Buffer Overflow
As discussed above, C and C++ doesn't perform a size check on a variable, therefore a program can exceed the size boundary for a variable while defining a value for it. Consider following program.
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#define MAX_WORD_LENGTH 5
int main(int argc, char *argv[])
{
char password[5];
int authenticate = 0;
printf("Enter a word (<%d chars): ", MAX_WORD_LENGTH);
fflush(stdout);
scanf("%s", password); /* DANGER: vulnerable to buffer overflow*/
if(strcmp(password, "correct") == 0)
authenticate = 1;
if(authenticate)
printf("You are authorized");
}
As you can see, that the length of string password is initially defined as 5. On a 32 bit processor, it will be allocated 8 bytes. The variable authentication is declared and defined right after password, it will be pushed on next stack position and will also be allocated 8 bytes.
Buffer Overflow Attack!
If during the runtime a user inputs more than 5 characters for password, lets say following
wrongpass1
The first eight characters (a byte is allocated for each character) will be used for variable password and the ninth character will be used for the variable authenticate. That means by using a malformed input, we can define value for next variable on the stack.
This is a very simple example of a buffer overflow attack. However, a buffer overflow attack can be as deadly as hijacking root level access for the host system.
Defenses
Defenses against buffer overflow attacks are canaries, tagging and bound checking. Going over the defenses is beyond the scope of this article.
Disclaimer
This article is written for educational and awareness purpose.